Ransomware is everywhere — even in this sleepy Texas town
- Share via
KEENE, Texas — When a ransomware attack hit Keene, Texas, no one noticed.
Like many small Texas cities, Keene — an exurb about 40 miles south of Fort Worth with a population of about 6,500 — contracted its technology services to an out-of-town company, including management of its computer servers. The city had never been hit with something like this before.
So when Landis Adams and other city employees showed up as usual at 8 a.m. Friday, turned on their computers and saw a mess of text, they figured the servers were down.
But when city officials contacted the company that manages their server, they learned they were among several cities experiencing problems. The computer systems of more than 20 small Texas municipalities were paralyzed in a coordinated cyberattack.
“We’re not prepared for something like that — most cities in America are not,” Adams, the city spokesman and economic development director, said Tuesday.
The Texas Department of Information Resources has worked over the last few days to help cities get back online; about a quarter of those hit have begun to recover, with some of the infected systems back to normal operations as of Tuesday afternoon, according to a news release from the department.
Officials did not reveal the names of the local governments affected or other details about the attack, beyond identifying the attacker as a “single threat actor.” It doesn’t appear to be a coordinated large-scale attack on the state, said FBI spokeswoman Melinda Urbina. Authorities see it more as a sophisticated financial scam that happened to various cities.
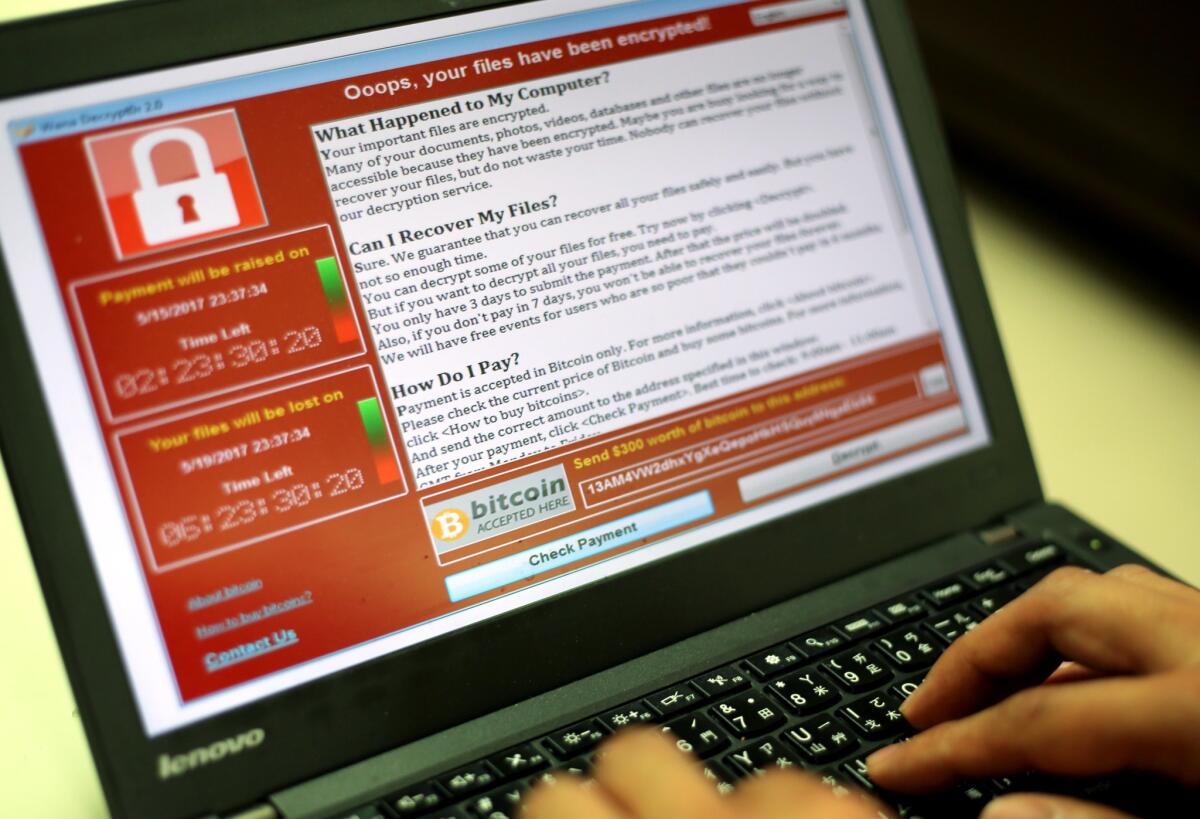
In ransomware attacks, hackers use a type of malware, or malicious software, to encrypt files, essentially placing a victim’s computer or network behind lock and key. Perpetrators often demand ransom in exchange for a decryption key that supposedly will restore access.
Adams said he didn’t know whether the attacker had demanded a ransom or set a deadline for payment. If so, the city doesn’t plan to pay.
Instead, the city is relying on the state to restore its computers from backups, Adams said.
Most city services in Keene — such as 911, police and utilities — were not affected. The attack prevented the city from accepting credit-card payments for water bills, so it suspended billing and disconnections until the computer system is brought back online, Adams said. He posted statements online, reassuring Keene residents that the attack had not compromised water quality or their personal information.
One other city besides Keene has publicly announced its systems were affected. A news release from officials in Borger, in the Texas Panhandle, said the attack had affected city business and financial operations, though the city has continued to provide basic emergency services such as police and fire response. Birth and death certificates are not available online, and the city can’t accept utility payments.
“Responders have not yet established a time frame for when full, normal operations will be restored,” city officials said in the release.
Ransomware attacks have been on the rise since they burst on the scene around 2012.
In 2016, Hollywood Presbyterian Medical Center was hit with an attack. Devices and medical records were locked until the hospital paid $17,000 in bitcoin.
In May 2017, the WannaCry ransomware infected about 200,000 computers across 150 countries. The attack also crippled the United Kingdom’s National Health Service and the networks of companies such as Boeing and Honda. Similar attacks hit the Port of Long Beach in July and the Port of San Diego in September.
Attacks this year hit Albany, N.Y., Greenville, N.C., Baltimore and three Florida cities. In July, ransomware infected Georgia’s court system and state and Capitol police.
It’s easy to perpetrate a ransomware attack, said Maya Levine, a Check Point security engineer.
“You can buy fully weaponized ransomware malware on the dark web for $20,” she said. “All you have to do is email it out.”
Often computer systems are infected through these phishing schemes — fake email attachments that appear legitimate but contain malicious code.
Scammers don’t discriminate, said FBI spokeswoman Laura Eimiller. Everyone is vulnerable including hospitals, school districts, private companies and individuals.
“It’s a problem for anyone who has a computer or a computer network,” Eimiller said.
However, the targets that make the most sense are those whose operations rely heavily on continuity — where day-to-day operations are crucial, such as hospitals that rely on computers to monitor treatments, said Rodrigo Bijou, a senior manager at Gap’s Cyber Defense Center.
At least 170 county, city or state government systems have experienced a ransomware attack since 2013, and 22 of those attacks occurred in 2019 alone, the U.S. Conference of Mayors reported in July. Mayors from across the U.S. have pledged to not pay future ransom demands. The agreement came after several high-profile ransomware attacks.
Small cities might be appealing targets since they often lack the resources to prioritize information security, Levine said.
Most entities will consider paying the ransom because it’s the least painful option, Bijou said. It can cost a municipality hundreds of thousands of dollars to hire an information security firm to get its systems running again. “Paying the ransom ends up being a lot cheaper and more effective,” he said, though the FBI is “always going to say they’re against it.”
The FBI discourages paying ransoms, saying there is no guarantee the decryption key will restore systems as promised. Also, experts say paying cyber criminals might encourage similar crimes.
Two Florida cities recently paid a total of more than $1 million in cryptocurrency to get access to their data. Lake City paid about $460,000 in bitcoin and Riviera Beach agreed to pay $600,000 in ransom.
News of the attack spread slowly in Keene. Joe Erzo, 50, a truck driver and Keene resident, learned what happened when his wife tried to pay the family’s water bill and was turned away.
“It’s a good little town. Not a lot of things happen — the crime is really low,” he said. “They’re looking for an easy target, I guess.”
On Tuesday, the state sent technicians to Keene’s red-and-yellow brick City Hall. They went from office to office, checking computers for ransomware.
“After all of this is over and the smoke clears, hopefully we can learn more about preventive things we can do” to avert another attack, Adams said.
More to Read
Sign up for Essential California
The most important California stories and recommendations in your inbox every morning.
You may occasionally receive promotional content from the Los Angeles Times.















